Hacking Metasploitable #1: Introduction & IRC Hack [Metasploit/Linux/Exploit/How-to]
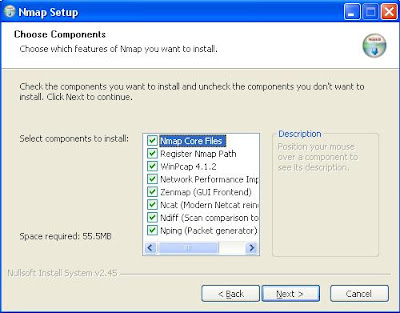
Starting today, I will start releasing how-tos on hacking the Metasploitable distro of Linux released by the creators of Metasploit in which I will go through how to determine if a system is exploitable, how to use Metasploit, how to load modules and run exploits, and what to do once you have exploited a system. I hope these posts, starting with this (#1), teach the readers the important parts of using Metasploit as well as the basics of Pentesting and exploitation. This is by no means a thorough series on exploitation, but a way to get basic users' hands wet in the world of exploitation and hacking.